The certificate chain of trust is a hierarchical structure that ensures the authenticity and integrity of SSL certificates.
It establishes trust between the end entity and the client such as a browser by verifying the certificate’s validity.
This tutorial explains how certificate chaining works and how a browser determines that your certificate can be trusted.
In order for an SSL certificate to be trusted, it has to be traceable back to the trust root it was signed off of. The chain or path begins with the SSL/TLS certificate, and each certificate in the chain is signed by the entity identified by the next certificate in the chain.
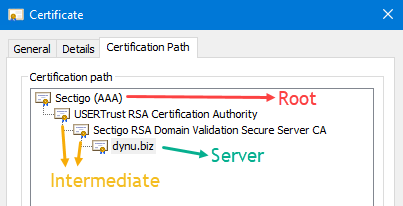
Root CA Certificate – A root certificate is a digital certificate that is signed by the issuing Certificate Authority itself. It usually comes pre-installed in most browsers and is stored in the trust store.
Intermediate Certificate – Any certificate that sits between the Server Certificate and the Root Certificate is called a chain or Intermediate Certificate. There will always be at least one intermediate certificate in a chain, but there can be more than one. The Intermediate Certificate is the signer/issuer of the Server Certificate. The Root CA Certificate is the signer/issuer of the Intermediate Certificate.
Server Certificate – The server certificate is the one issued to the specific domain.
When you order your SSL certificate, you will be provided with the Server Certificate (yourdomain.crt) as well as the intermediate certificates (intermediate.crt). When visitors access your secure site, their browser initiates an SSL Handshake process. The browser verifies your SSL certificate: It checks the digital signatures of the issuing CAs, tracing the chain up to the trusted Root CA. If the certificate is valid and can be chained back to a trusted root, it will be trusted. If it can’t be chained back to a trusted root, the browser will issue a warning about the certificate.
You will receive errors regarding your certificate’s Chain of Trust if something has been misconfigured. We have a SSL checker tool that can tell you exactly which link is broken in the chain of trust.
Here are some things to consider if you receive an error relating to your trust chain:
Was your SSL certificate issued by a trusted CA? Self-signed certificates can often face this issue.
Did you install your intermediates properly? While some browsers try to fill in any gaps in the certificate chain, you still need to make sure that you successfully install all intermediate certificates.
Is your server configured correctly? Though you may have installed the SSL certificate and any accompanying intermediates, you may not have configured your server properly.
What is chain of trust?
In order for an SSL certificate to be trusted, it has to be traceable back to the trust root it was signed off of. The chain or path begins with the SSL/TLS certificate, and each certificate in the chain is signed by the entity identified by the next certificate in the chain.

Root CA Certificate – A root certificate is a digital certificate that is signed by the issuing Certificate Authority itself. It usually comes pre-installed in most browsers and is stored in the trust store.
Intermediate Certificate – Any certificate that sits between the Server Certificate and the Root Certificate is called a chain or Intermediate Certificate. There will always be at least one intermediate certificate in a chain, but there can be more than one. The Intermediate Certificate is the signer/issuer of the Server Certificate. The Root CA Certificate is the signer/issuer of the Intermediate Certificate.
Server Certificate – The server certificate is the one issued to the specific domain.
How does the Chain of Trust work?
When you order your SSL certificate, you will be provided with the Server Certificate (yourdomain.crt) as well as the intermediate certificates (intermediate.crt). When visitors access your secure site, their browser initiates an SSL Handshake process. The browser verifies your SSL certificate: It checks the digital signatures of the issuing CAs, tracing the chain up to the trusted Root CA. If the certificate is valid and can be chained back to a trusted root, it will be trusted. If it can’t be chained back to a trusted root, the browser will issue a warning about the certificate.
Troubleshooting Chain of Trust Issues
You will receive errors regarding your certificate’s Chain of Trust if something has been misconfigured. We have a SSL checker tool that can tell you exactly which link is broken in the chain of trust.
Here are some things to consider if you receive an error relating to your trust chain:
Was your SSL certificate issued by a trusted CA? Self-signed certificates can often face this issue.
Did you install your intermediates properly? While some browsers try to fill in any gaps in the certificate chain, you still need to make sure that you successfully install all intermediate certificates.
Is your server configured correctly? Though you may have installed the SSL certificate and any accompanying intermediates, you may not have configured your server properly.
